Security Reports
Generate compliance reports for CISOs, stakeholders, and auditors. Get OWASP LLM Top 10 coverage, SOC2 mapping, and audit trails.
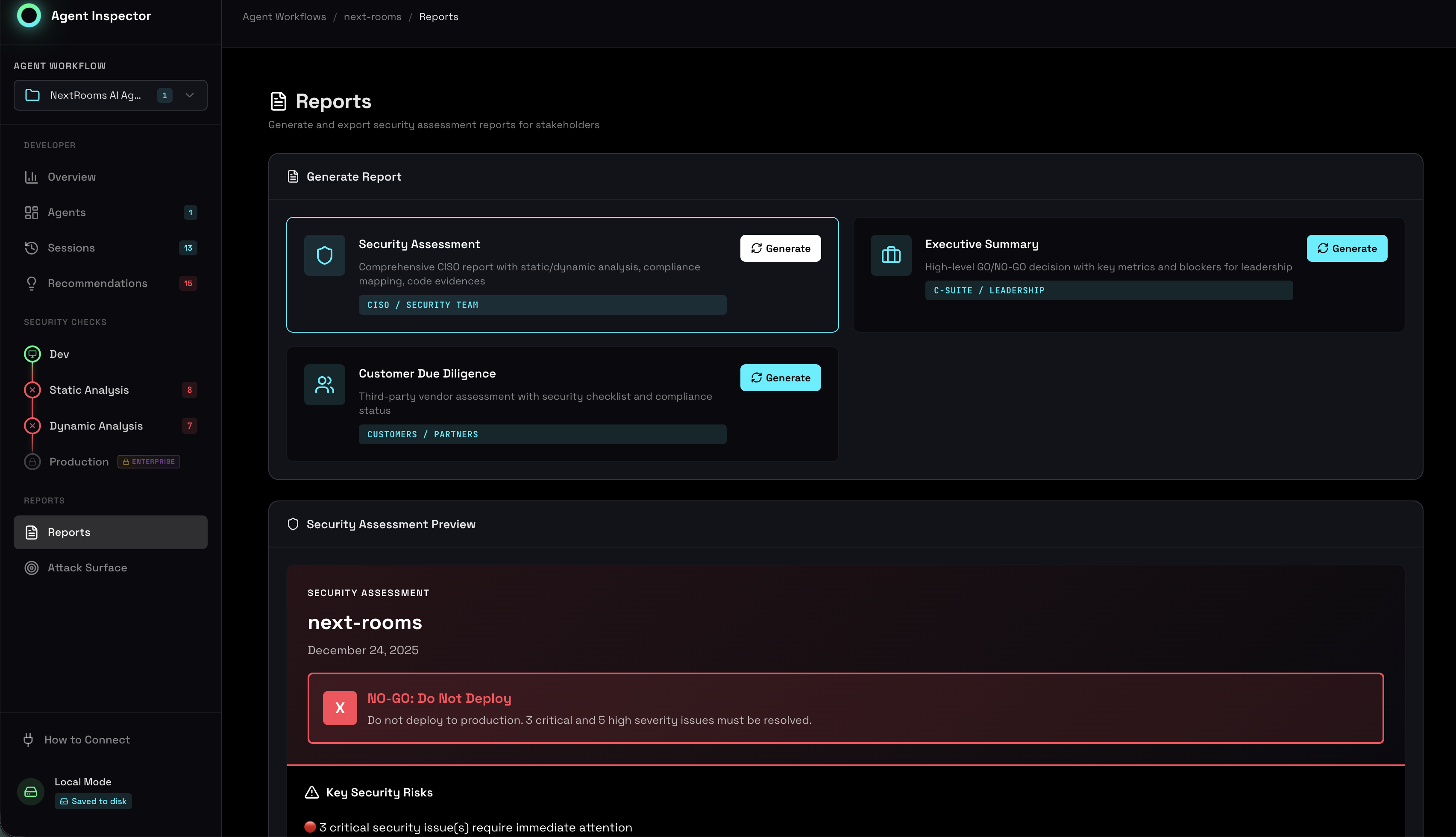
Report Types
Agent Inspector generates three types of reports for different audiences:
Security Assessment
For: Security teams, technical auditors
- All findings with full technical details
- Code locations and remediation steps
- Correlation evidence
- OWASP LLM category mapping
- CWE references
Executive Summary
For: CISOs, board members, leadership
- High-level risk posture
- Aggregate scores and trends
- Remediation progress
- Production readiness status
- Key metrics and KPIs
Customer Due Diligence
For: Customers, prospects, partners
- Security practices overview
- Compliance certifications
- Assessment methodology
- Evidence of security testing
- Redacted technical details
Generate a Report
/agent-report security-assessment
/agent-report executive-summary
/agent-report customer-dd
OWASP LLM Top 10 Coverage
Reports show your coverage against the OWASP LLM Top 10 framework:
| ID | Category | Coverage |
|---|---|---|
| LLM01 | Prompt Injection | Static + Dynamic |
| LLM02 | Insecure Output Handling | Static + Dynamic |
| LLM03 | Training Data Poisoning | Static only |
| LLM04 | Model Denial of Service | Static + Dynamic |
| LLM05 | Supply Chain Vulnerabilities | Static + Dynamic |
| LLM06 | Sensitive Information Disclosure | Static + Dynamic |
| LLM07 | Insecure Plugin Design | Static |
| LLM08 | Excessive Agency | Static + Dynamic |
| LLM09 | Overreliance | Static |
| LLM10 | Model Theft | Static |
SOC2 Compliance Mapping
Reports map findings to SOC2 Trust Service Criteria:
CC6 - Logical Access Controls
- Tool permission checks
- Input validation
- Output sanitization
CC7 - System Operations
- Rate limiting
- Resource management
- Error handling
PI1 - Privacy Information
- PII detection
- Data handling
- Logging practices
CC9 - Risk Mitigation
- Vendor risk (supply chain)
- Model validation
- Security testing evidence
Report Contents
Security Assessment Report
- Executive Summary: Risk score, key findings, recommendation summary
- Findings Detail: Each finding with severity, category, location, evidence
- Correlation Analysis: VALIDATED, UNEXERCISED, THEORETICAL breakdown
- OWASP Coverage: Category-by-category analysis
- Remediation Status: PENDING, FIXING, FIXED, VERIFIED counts
- Production Gate: GO/NO-GO status with blocking issues
- Audit Trail: All fixes, dismissals, and approvals with timestamps
Executive Summary Report
- Risk Dashboard: Overall security score with trend
- Key Metrics: Findings by severity, remediation rate, coverage %
- Progress: Week-over-week improvement
- Blockers: Top issues requiring attention
- Recommendations: Action items for leadership
Customer DD Report
- Security Practices: Overview of security methodology
- Testing Evidence: Proof of security assessment
- Compliance: Framework coverage (OWASP, SOC2)
- Risk Posture: Summary without sensitive details
- Certifications: Any relevant certifications
Export Formats
Reports are available in multiple formats:
| Format | Use Case |
|---|---|
PDF |
Formal documentation, board presentations, customer delivery |
HTML |
Interactive viewing, internal sharing |
JSON |
API integration, programmatic processing |
CSV |
Spreadsheet analysis, data import |
# Generate PDF report /agent-report security-assessment --format pdf # Generate JSON for API /agent-report executive-summary --format json
For Developers
IDE Commands
# Generate reports /agent-report security-assessment /agent-report executive-summary /agent-report customer-dd # Specify format /agent-report security-assessment --format pdf # Include specific agent only /agent-report security-assessment --agent my-agent-workflow
API
# Generate report via API
curl -X POST http://localhost:7100/api/reports \
-H "Content-Type: application/json" \
-d '{"type": "security-assessment", "format": "pdf"}'
# Download generated report
curl http://localhost:7100/api/reports/report-id/download
Scheduling
For CI/CD integration, generate reports automatically after analysis:
# After running tests and analysis agent-inspector report security-assessment --output ./reports/ agent-inspector report executive-summary --output ./reports/
Reports dashboard showing available report types and history